Introduction
Don’t you hate remembering all of your passwords? With OpsLevel’s Single Sign-On integration all of your microservice data is seconds away without the need for another long and secure password.
With single sign-on, you get:
- Automatic user provisioning: OpsLevel will create a user for you as long as the employee has access to the OpsLevel application in your identity provider.
- Revoke user access: Removing a user’s access from OpsLevel is as simple as revoking their access in your identity provider.
Using Google, Auth0 or Okta?
Checkout our guides on how to configure Google, Auth0 or Okta alongside OpsLevel!
Setting up Single Sign-On with SAML
The following metadata URL can be used to help automate the configuration of SAML within your identity provider. Note: You will need your provider_key, located in your Account Settings under Authentication Method
https://app.opslevel.com/users/auth/saml/metadata?provider_key={provider_key}
Required Identity Provider Attributes
- Destination: Sometimes labeled as
Recipient URLorSingle Sign-On URL. This will be the URL OpsLevel will receive the SAML response to. This value is located in your Account Settings under Authentication Method:https://app.opslevel.com/users/auth/saml/callback?provider_key={provider_key} - Audience: Sometimes labeled as
Audience RestrictionorSAML Audience. This field should be configured to:opslevel - Email: The user’s email address. This is expected as an attribute with a
namevalue ofemail
Auto-Provisioning Attributes
In order to have users auto-provisioned when they first sign in, we require the following optional attributes:
first_name: The given name of the user.last_name: The family name of the user.
OpsLevel Configuration
Any admin user on your OpsLevel account may configure the SAML single sign-on settings by:
- Navigating to the Authentication Method section of the Account Settings page.
- Selecting
Editat the bottom of the card.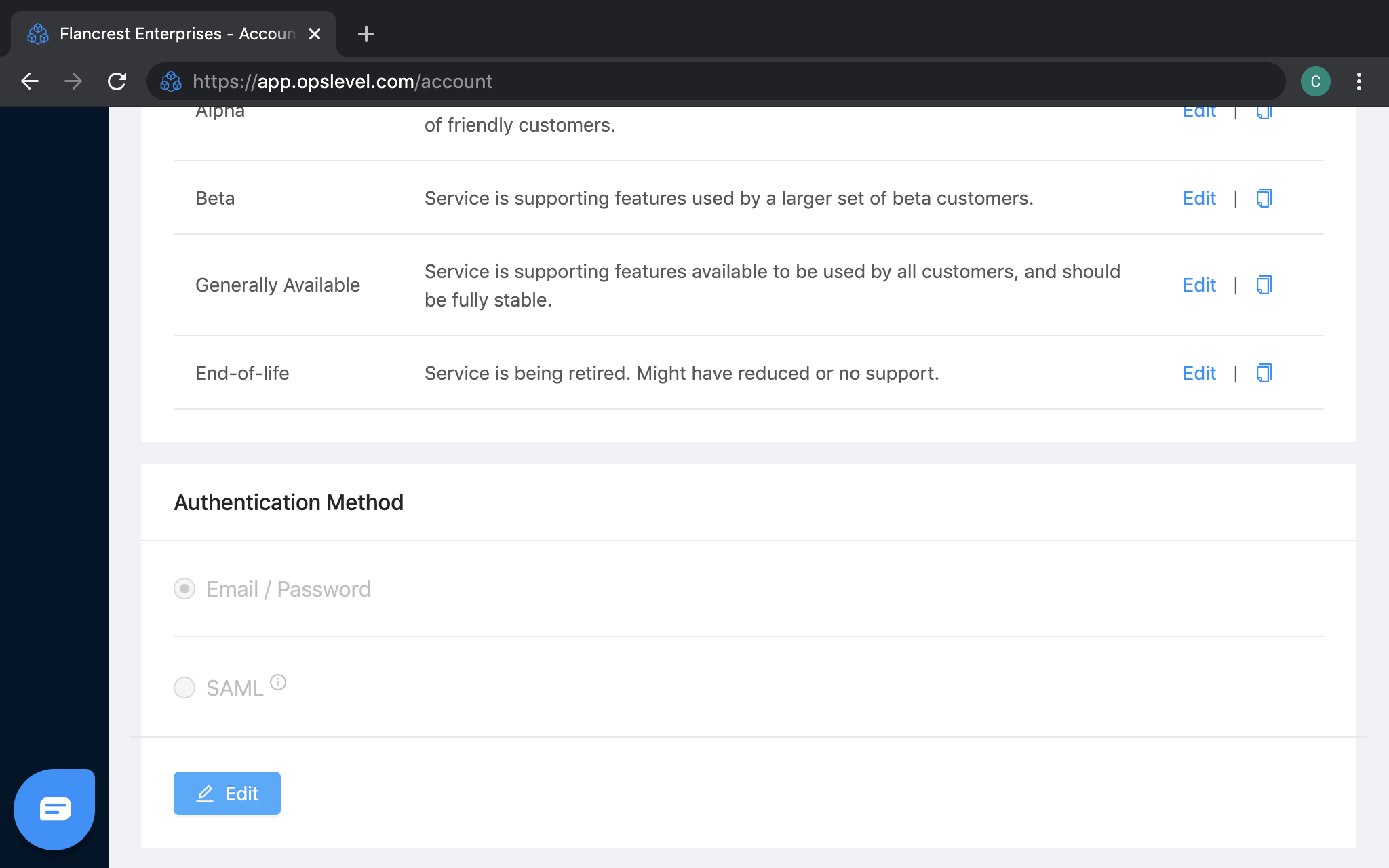
- Clicking on the option labeled
SAML - Specifying the corporate email domain used by your company under:
Email Domain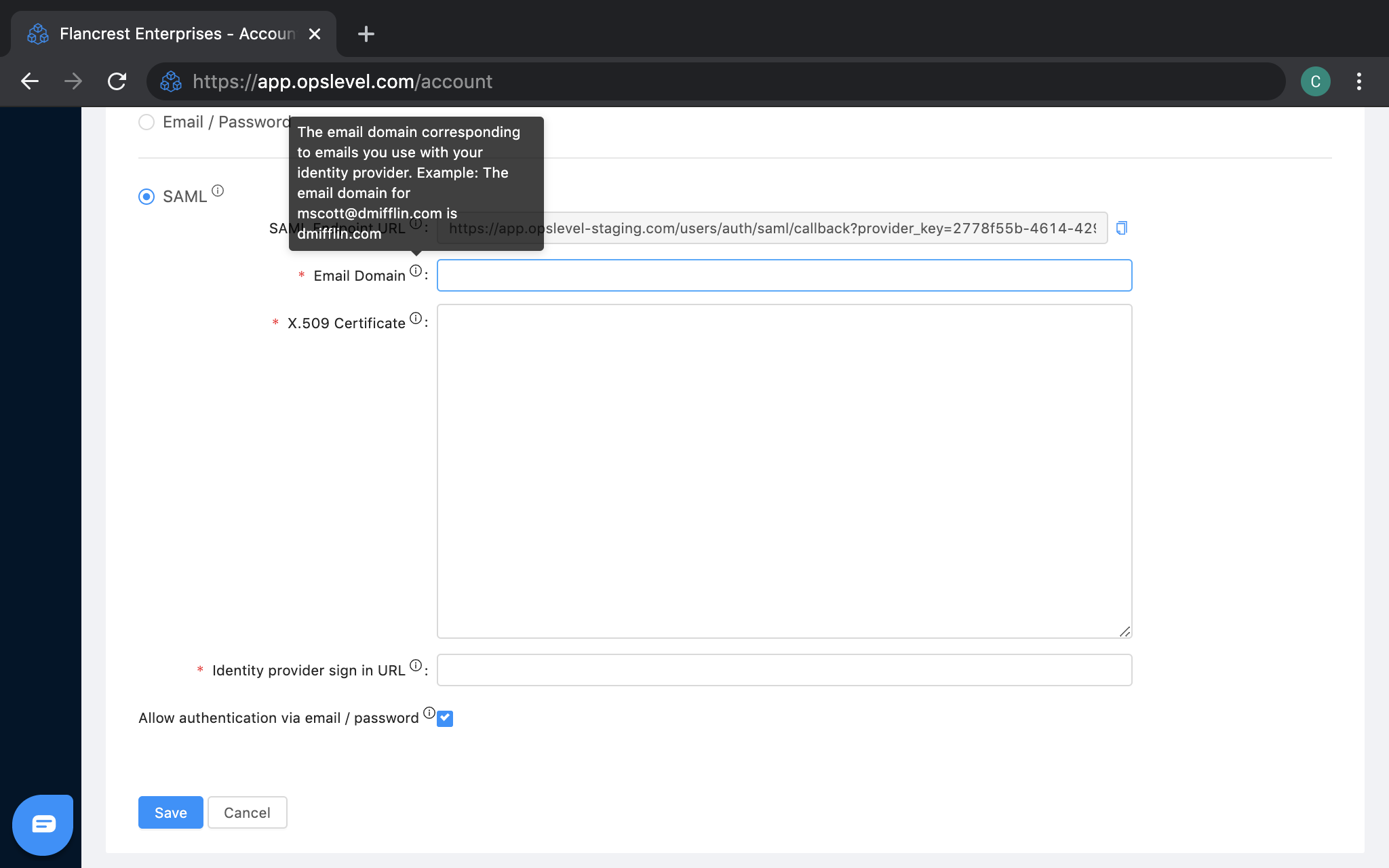 .
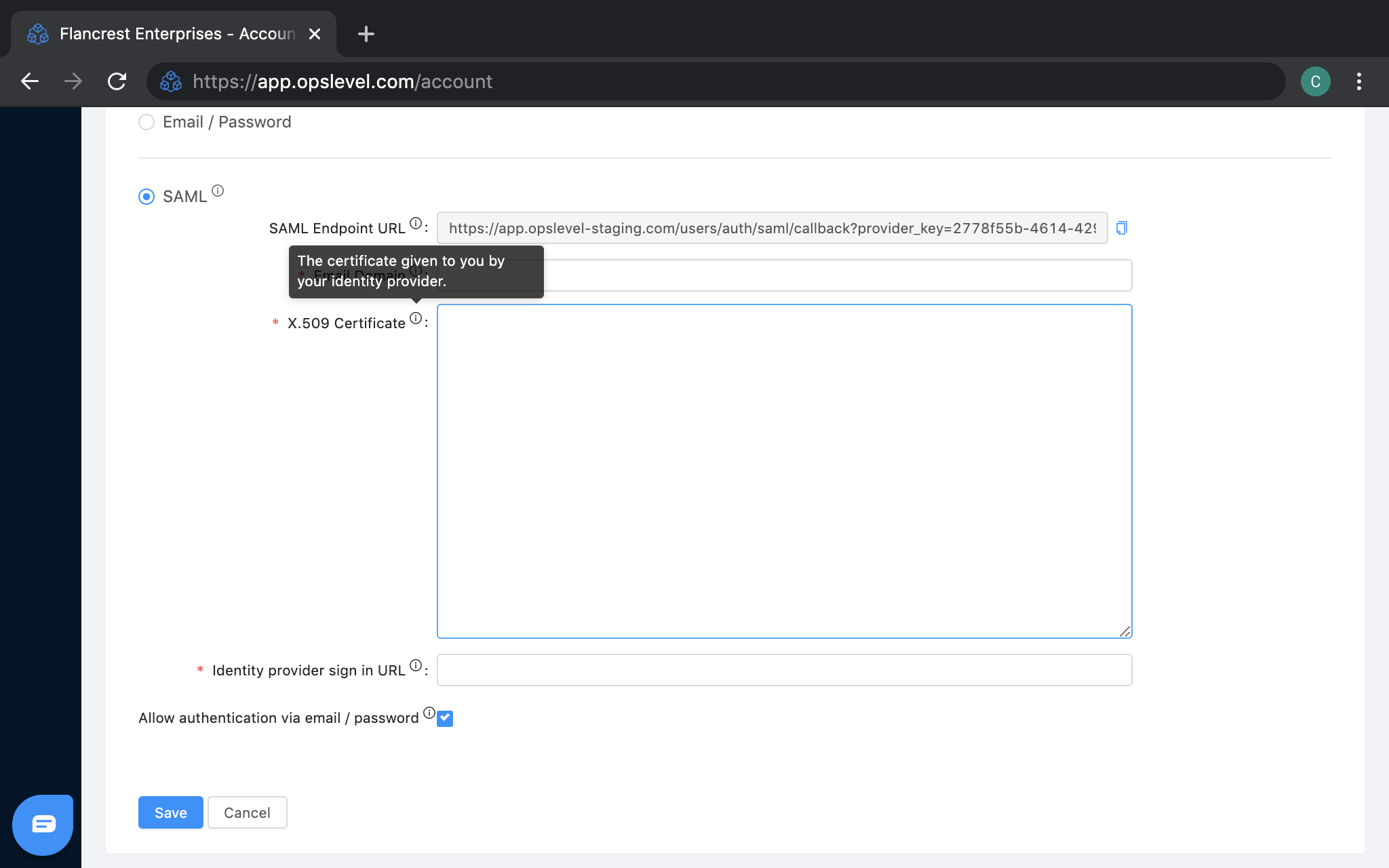
. - Pasting in the X.509 Certificate from the SAML configuration in your identity provider.
- Pasting in the Single Sign-on URL from the SAML configuration in your identity provider.
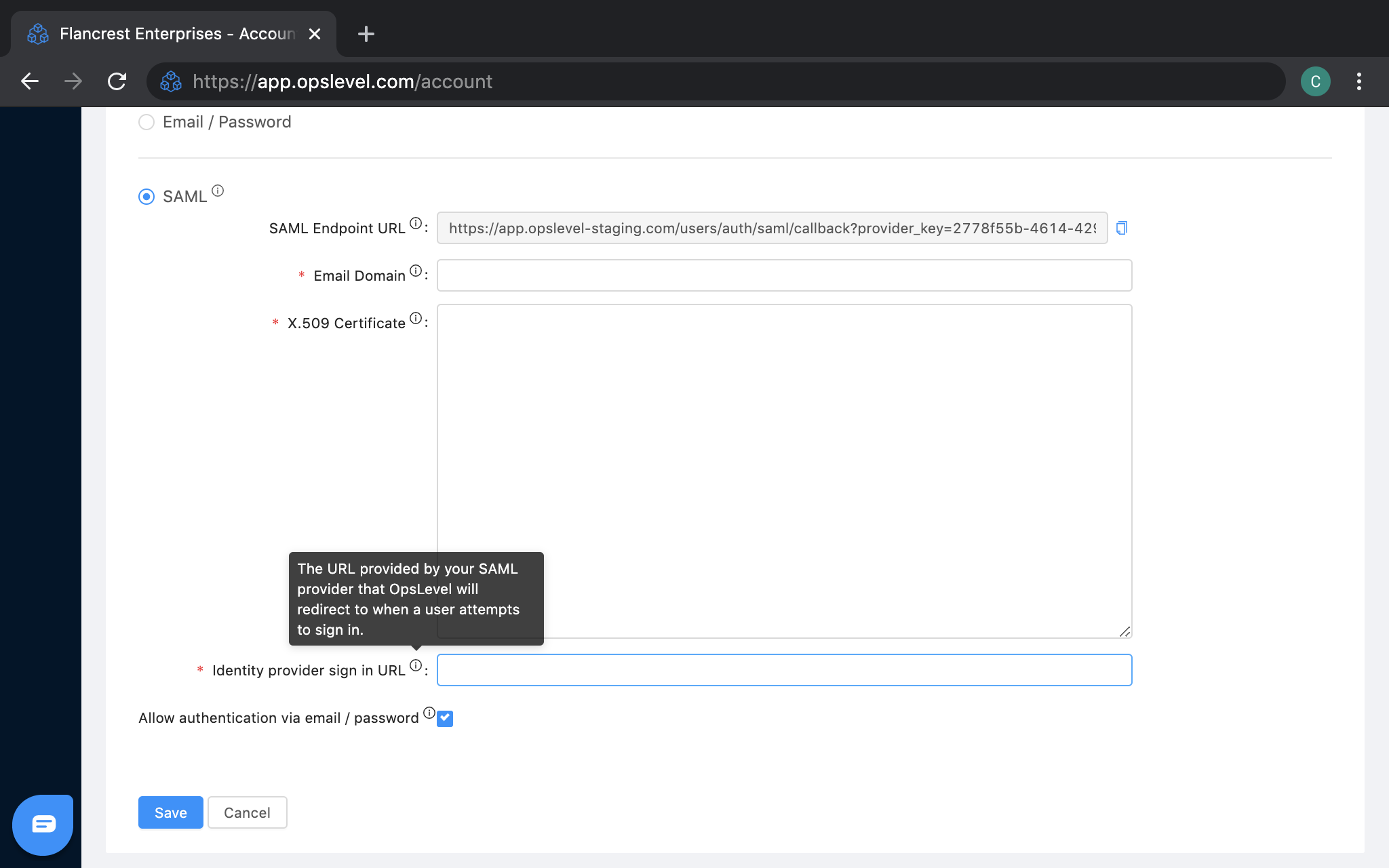
- (Optional) De-selecting
Allow authentication via email / passwordonce your configuration has been verified as operational.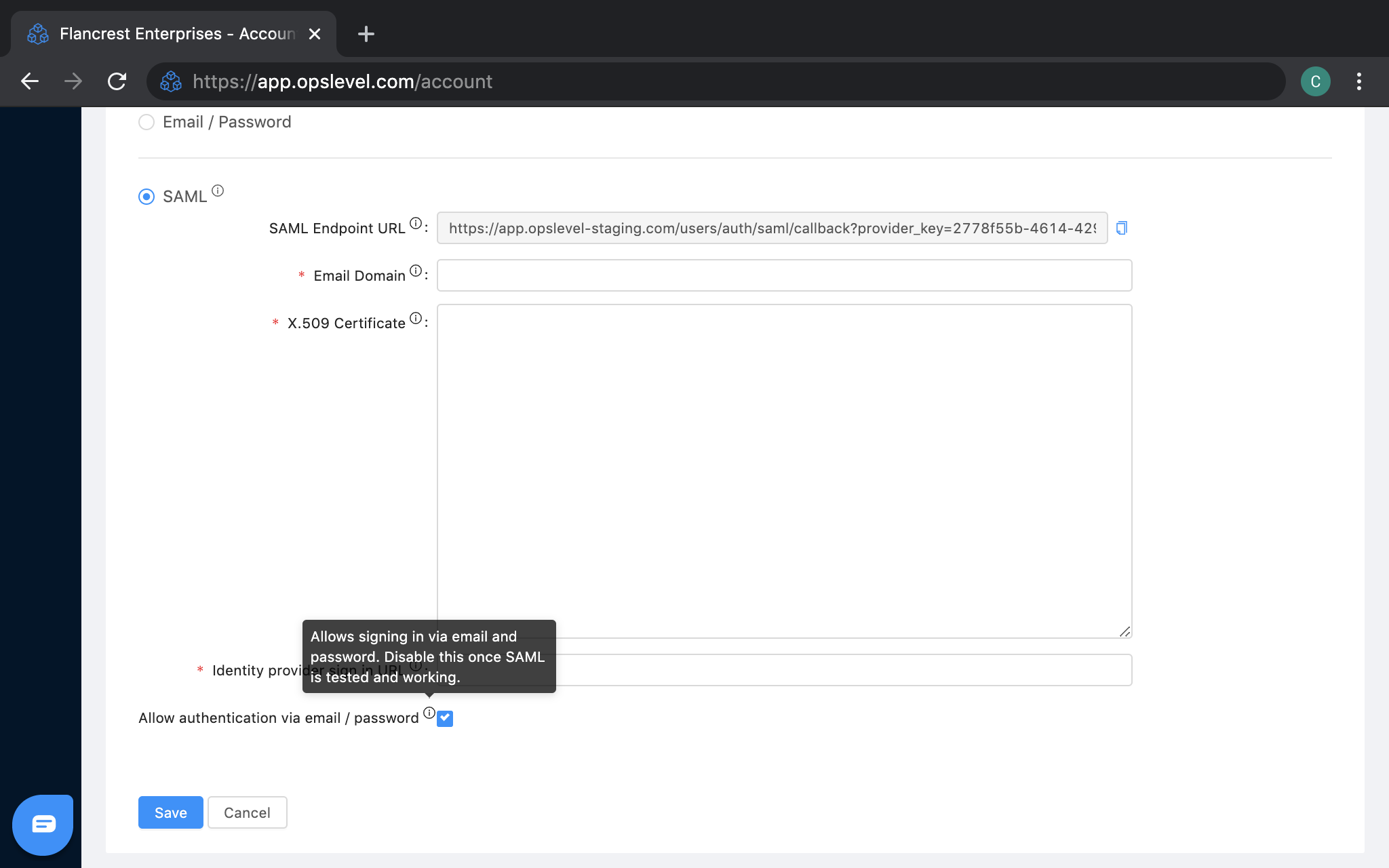
Log in via Single Sign-on
- Navigate to the OpsLevel Sign In Page.
- Select
Log in with SSO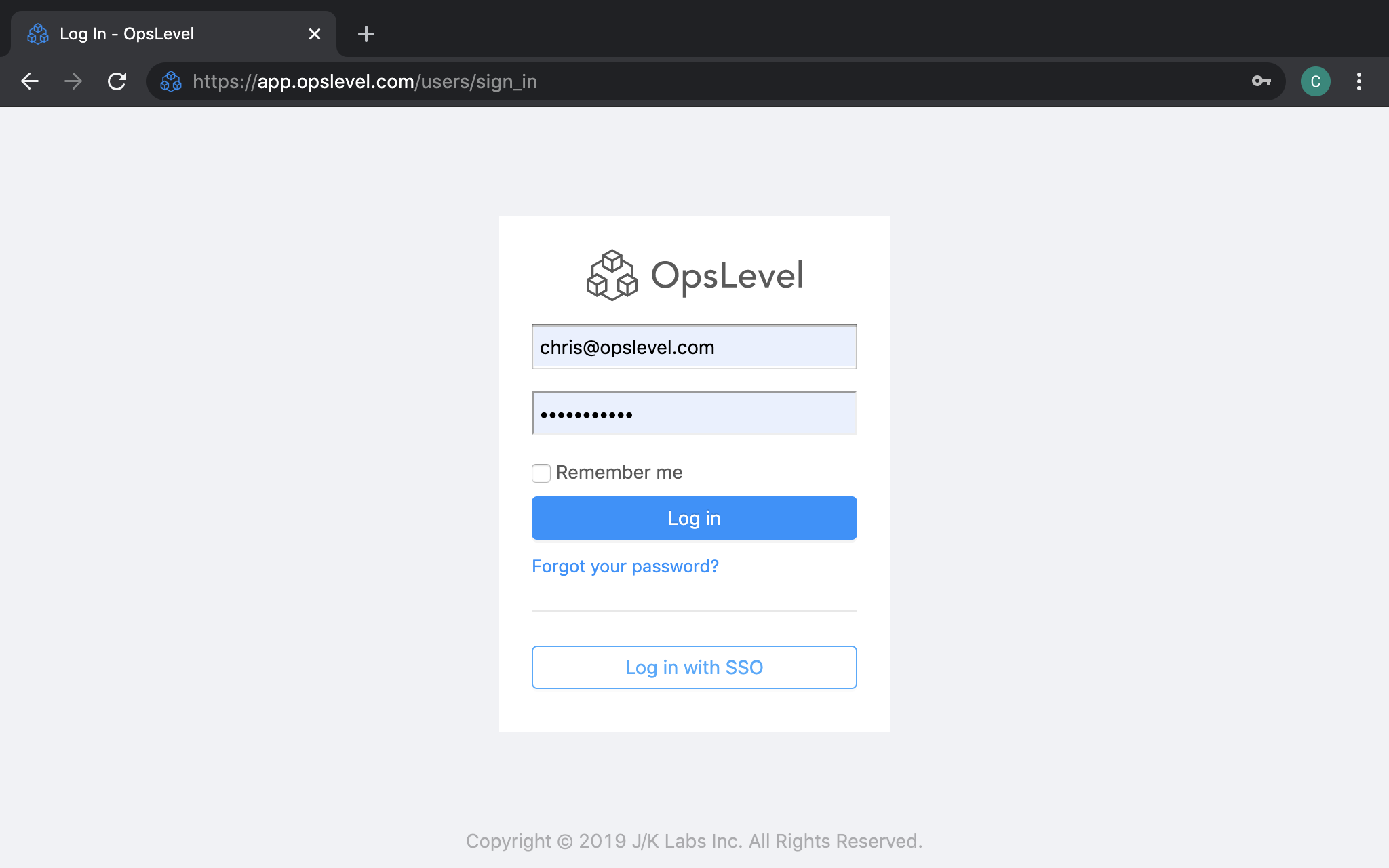
- Enter the email address associated with your company.
- Click
Log in with SSO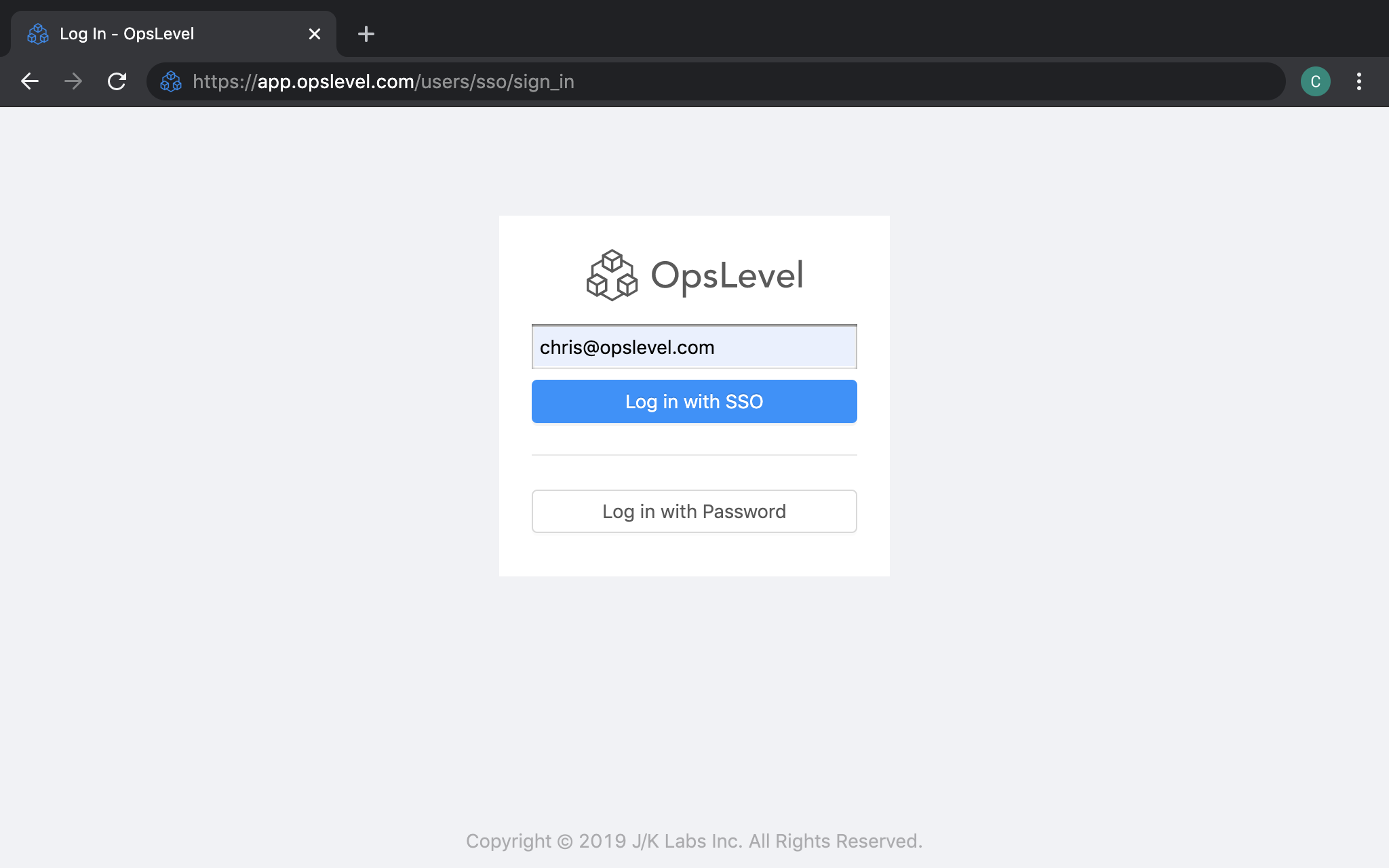
- If prompted, sign into your identity provider to complete the authentication request.
If you are having trouble setting up your single sign-on in any way, send us an email at info@opslevel.com and we’ll be happy to help debug and diagnose any issues.